14) which of the following are breach prevention best practices
Since cloud security is not widely understood it may be difficult to delineate it in the context of more general information security. Protects electronic PHI ePHI c.

Data Breach Response Times Trends And Tips
Best Practices for Enterprise Cloud Security.

. They need to be secure at the host eg. If you deal with private data regularly encryption is vital. Consider designating staff to carry out security monitoring.
A single technology cannot provide complete protection. To minimize these costs companies need to take preventative action to ensure that their systems are adequately protected. Department of Justice and elsewhere that client companies should consider to be fully prepared for the realities of a cyber-based attack.
He recommends campuses have firewalls. All of the above answer a. Maintaining a database of customer information leaves sensitive information vulnerable to outside threats.
Lets break down the top five practices companies can implement to prevent data breaches. Develop appropriate security measures Monitor compliance with required measures Comply with reporting requirements. Employee Training and Awareness.
You need to protect yourself against data breaches by creating a vendor-risk management program and policy that address the following. The following methods describe the best way a business owner can prevent data breaches in their companies. Limit reliance on static data.
Which of the following are breach prevention best practices. Which of the following are breach prevention best practices. Backup your data.
You should always logoff or lock your workstation when it is unattended for any length of time. Best Practices in Breach Prevention. Access only the minimum amount of PHIpersonally identifiable information PII necessary B.
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above correct 3 The minimum necessary standard. Typically a lot of breaches occur by the theft or loss of backup data which can be in the form of physical data like CDs or pen drives. Protect your most critical digital assets by segregating them and prioritizing them in your business continuity plan.
Best Practices for Preventing Data Breaches. Install an access management system to access the data. Full access to over 1 million Textbook Solutions.
S3 Breach Prevention. Ensure that your sensitive data is backed up regularly in case of a ransomware attack or system failure that causes loss of data. Data Breach Prevention for Healthcare - a Best Practices Guide Todays healthcare organizations are under pressure to increase the affordability quality and efficiency of patient care all while streamlining costs and staying compliant with ever-changing regulatory legislation.
Out of the box AWS offers. Attorneys should promote the following five best practices as gleaned from the US. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business associate BA b.
In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI. PCs cell phones PDAs and the network says Pappas. Addresses three types of safeguards - administrative technical and physical.
2 Which of the following are breach prevention best practices. For example sort data into groups such as confidential data general data internal data and external data and maybe even assign each with a distinct color then train employees to follow this system. What is the best.
System and data users are the weakest link in the implemented cybersecurity programs and the most vulnerable to data breach attacks. Initiate a program of employee training. Training employees in cybersecurity awareness is essential to guard against social engineering attacks.
Data Breach Response Guide at p. Regular backups of your most sensitive data should be a part of this IRP to help you mitigate the damages a data breach could cause to business functions. A Look at the Security Rule Security Risk Analysis Breaches and Notification OCR Audit Program.
Institute report suffering at leas t one data breach in the past 2 years Data breaches could be costing the healthcare industry upwards of 62 billion per year A breach of medical information costs healthcare organizations an average of 22 million per breach Interestingly the value of medical information on the black market has. Do you have strong password policy and is it being adhered to. 247 help from Expert Tutors on 140 subjects.
See Page 1. Breach prevention best practices for the prevention of. Those who use SharePoint best practices often follow Microsoft ones too because of their safety and security.
Access to over 100 million course-specific study resources. One of the most common causes of a data breach is weak password policies. Which of the following are breach prevention best practices.
All of this above. Which of the following are examples of personally identifiable information PII. Other terms for this phenomenon include unintentional information disclosure data leak information leakage and also data spillincidents range from.
A Summary of Cybersecurity Best Practices at p. When a data breach occurs involving a cloud service the impulsive reaction is to denounce using the cloud at least for sensitive information. There are Microsoft best practices best practices and practices.
Password policies that include regular rotation and high levels of. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary andby promptly retrieving documents containing PHIPII from the printer.

Which Of The Following Are Breach Prevention Best Practices Public Health

Analyzing Company Reputation After A Data Breach

Board Oversight Of Cyber Risks And Cybersecurity Imd Article

6 Most Common Causes Of Data Leaks In 2022 Upguard

Orca Security Launches Industry S First Cloud Risk Encyclopedia To Provide Ongoing Education For Cloud Security Best Practices Business Wire

Analyzing Company Reputation After A Data Breach

Preventing Hipaa Data Breaches Case Studies And Best Practices

Recent Cyber Attacks Data Breaches In 2021

6 Steps To Developing A Data Breach Response Plan Spectral

Top 4 Human Errors In Cyber Security How To Prevent Employee Mistakes Ekran System

Insufficient Logging And Monitoring Ultimate Guide 2022

Law Firm Cybersecurity Compliance Requirements To Follow Ekran System
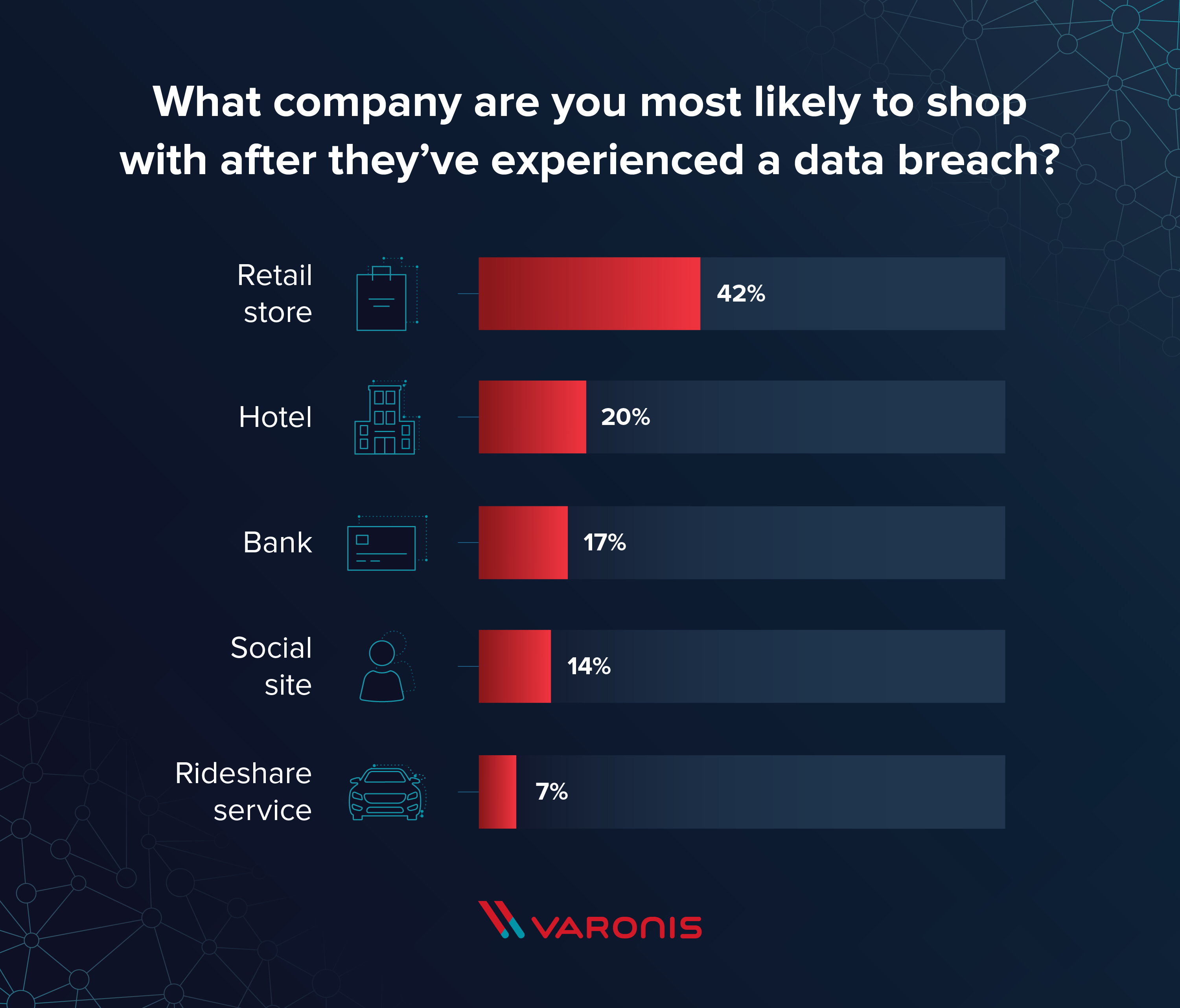
Analyzing Company Reputation After A Data Breach

How To Prevent Data Breaches In 2022 Upguard
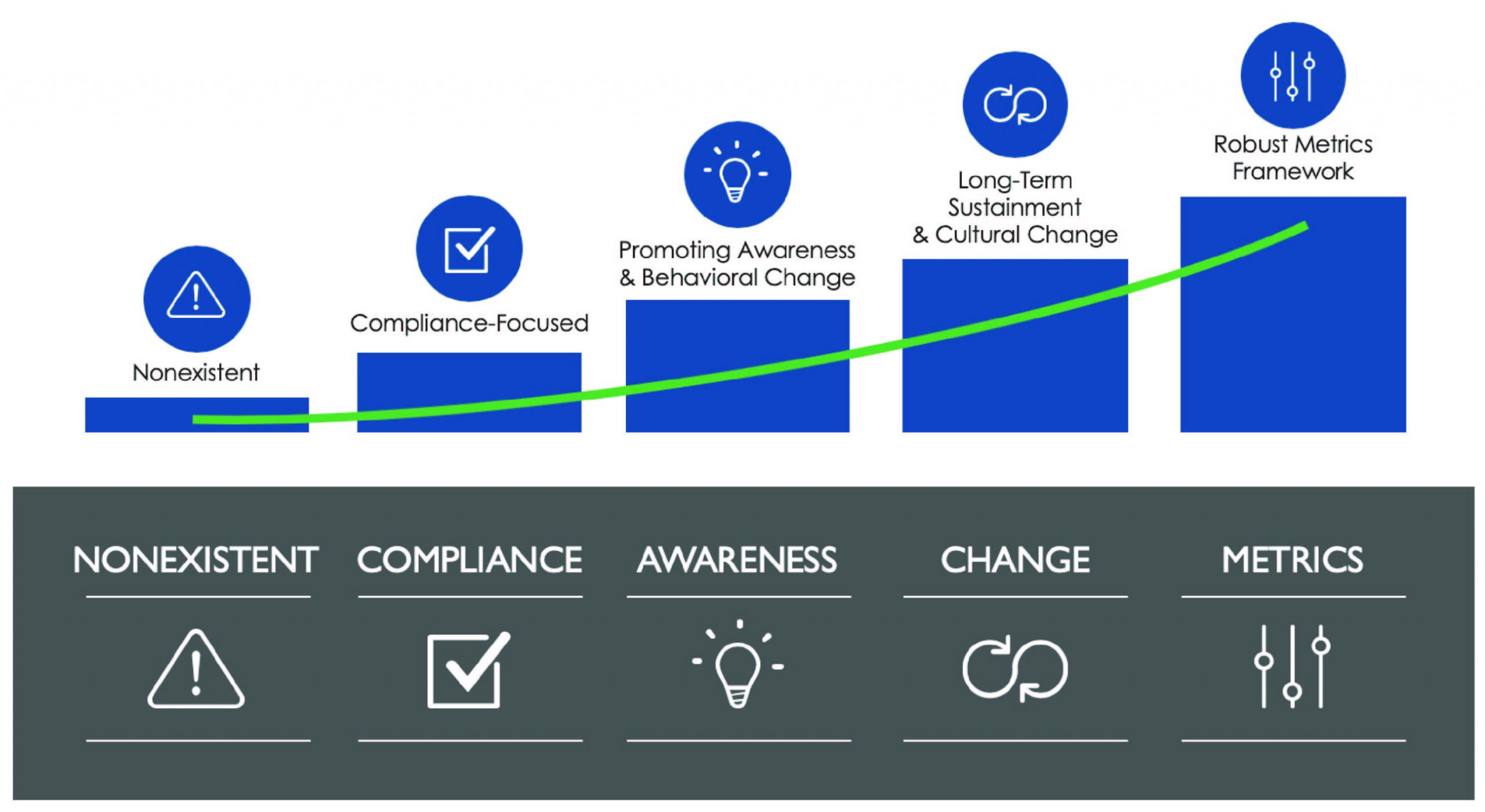
Best Practices For Building An Effective Security Awareness Program The Shi Hub

6 Most Common Causes Of Data Leaks In 2022 Upguard

Enterprise Data Breach Causes Challenges Prevention And Future Directions Cheng 2017 Wires Data Mining And Knowledge Discovery Wiley Online Library
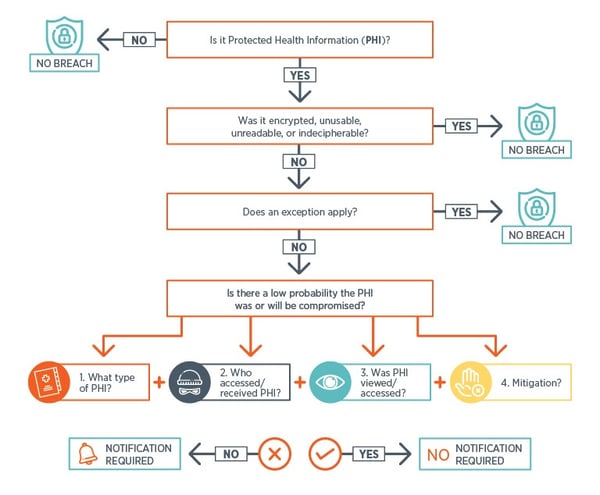
Preventing Hipaa Data Breaches Case Studies And Best Practices
